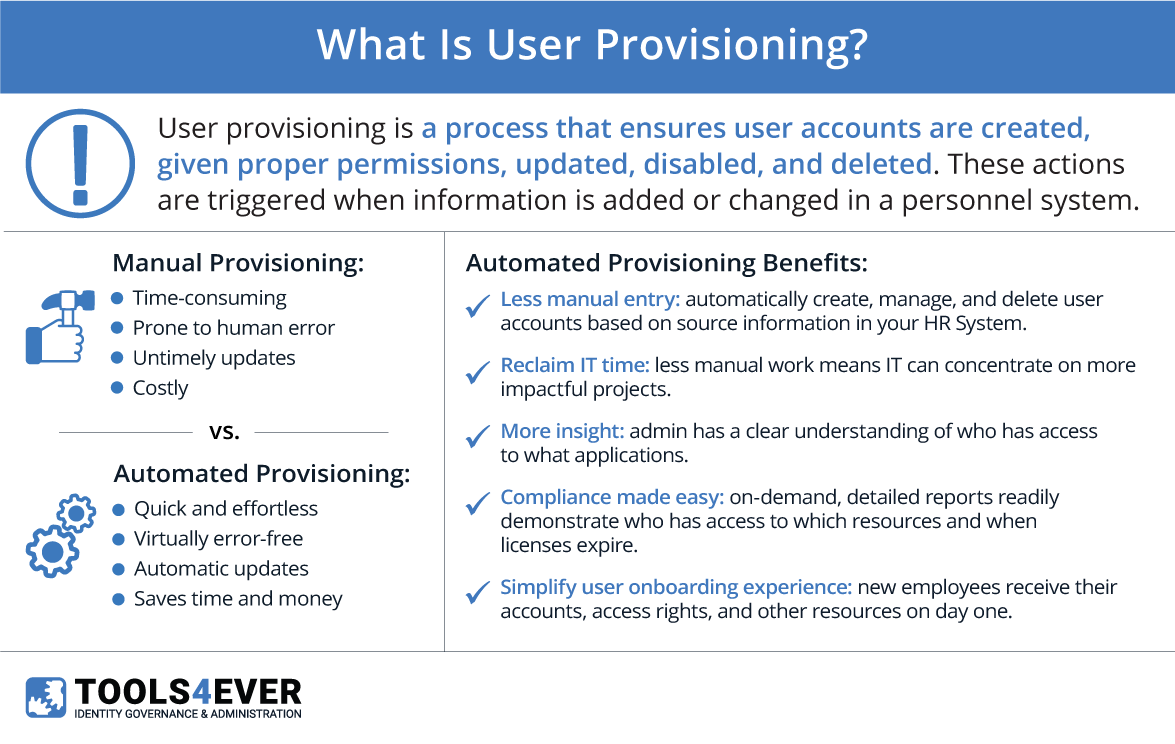
User Account Provisioning (or user provisioning) is an identity management process that ensures user accounts are created, given proper permissions, changed, disabled, and deleted. Automated User Account Provisioning is when these actions are triggered when information is added or changed in a “source system” (e.g., HR system).
New hires, promotions, transfers, and departures are examples of events that can trigger automated user account provisioning processes. When manually triggered, the process is also referred to as Delegated User Account Provisioning.
Manually managing user accounts, permissions, and the scope/reach of a granted permission can quickly become one of the IT department’s most time-consuming jobs. When a new person is hired, it takes the IT department an average of 30 minutes to create a new account and assign proper permissions. This process can be delayed by several days if the IT department is swamped with other tasks or if the account is not created correctly on the first try. This delay can leave a new employee stranded and unproductive on what was supposed to be their first day of work.
Creating new accounts occurs during onboarding is just one part of the whole account management process. When an employee changes their name, gets a promotion, or leaves employment, their account details and permissions must be audited and updated.
However, the revocation of irrelevant permissions from the user’s prior role is often not prioritized and, as a result, overlooked. This leads to an accumulation of access rights, which has become a major concern for security officers nowadays.
Automated User Provisioning
Automated provisioning removes the difficulties and delays caused by manually managing user accounts. For many organizations, the HR system is the first point of registration for employees. More and more, organizations adhere to a policy of, “if the employee is not present in the HR system, nothing will be done. The employee will not pass the company reception”.
As such, HR systems serve as organizations’ “single point of truth.” The next logical step is to use the HR system as the leading source for automating User Account Management tasks. And this is exactly what we do with our software. Our software is configured to look for changes in the personnel data, such as new employees, promotions, and name changes.
When these changes are detected, our software will automatically take action to create and maintain accounts throughout your network and related systems. These systems include directories such as Active Directory, Office 365, and Google G Suite, as well as business applications like SAP and Salesforce.
In addition to saving time and money, automated provisioning improves overall security. The HR system holds vital information about the employee’s role in the organization via the attributes of a job title, department, division, location, etc. The role determines what kind of IT services the employee needs to perform their job.
Within HelloID, “business rules” translate an employee’s attributes and role into the correct accounts, permissions, and scope of permissions their job requires. The exact required set. Not too less, but certainly not too many. Too much access leads to security and compliance risks, especially when it is accumulated over time and without revocation.
Automated Permission Assignment
In addition to user account provisioning systems, a comprehensive process will also manage the user accounts permissions across your network. This happens through a Business Role management process that combines personnel data with a configurable “role model” or “job matrix.” This attribute-based access control (ABAC) method determines users’ access to the IT services that correspond to the role they fulfill in the organization.
ABAC-based provisioning doesn’t stop at automatically granting IT services to new user accounts. In addition, it removes IT services that are no longer necessary for a user’s current job role. This removal of excess permissions greatly enhances security by reducing the risk of insider threats to your organization.i
Tools4ever’s identity management software tackles the issue of automated user provisioning and access management. Whenever there is a change in the HR system (e.g., new employee, name change, role change, leaving employment), our solutions trigger the appropriate process automatically. This makes account management quick, simple, secure, and cost-effective.
Automated Provisioning in the Real World
Let’s take a look at several real-world scenarios and how automated provisioning comes into play.
New Employee
When a new employee starts, they need an email account, a home directory, and group memberships. Depending on the employee’s role, other accounts may be necessary (e.g., SAP, Salesforce, ServiceNow).
The identity management system will generate a unique username, create a directory and email account, and a home directory on the appropriate file server. It will also add additional resources according to the user’s role and set them up for account claiming, if applicable.
Promotion
When an employee is promoted to a new position in the organization, IAM will update their directory account details as necessary. If they need additional accounts, those will be automatically created.
In addition, Business Roles will assign new permissions and remove old ones as necessary to avoid permission creep. This reduces the organization’s risk of a data breach and helps meet compliance requirements.
Employee Departures
When an employee leaves an organization, their accounts and access must be removed for security purposes (i.e., deprovisioning). The identity management system takes action to disable the ex-employee’s accounts and remove their access rights. Their accounts are typically held in isolation for a period of time before being permanently deleted.
Ad Hoc Requests
Not all access can be defined by the HR system. Sometimes a one-off is necessary. With a self-service solution, users and their managers can request access to additional systems and applications. The access request is then routed to the responsible party, who can approve or deny access with the click of a button. All without involving the IT department.
Software Solutions: HelloID
HelloID is Tools4ever’s flagship product, providing cloud-based user account provisioning and self-service workflows. Give your users streamlined application access and self-service capabilities no matter where they are in the world. Configurable approval workflows and dynamic forms let you customize the HelloID IDaaS experience to fit your organization’s unique needs.
