NIM: NexGen Identity Management
Enterprise IAM Software
Advanced Identity Management for Organizations with Complex, Multi-System Environments All Driven From “A Single Source of Truth”
A Powerful and Flexible Solution for Enterprises
User Provisioning
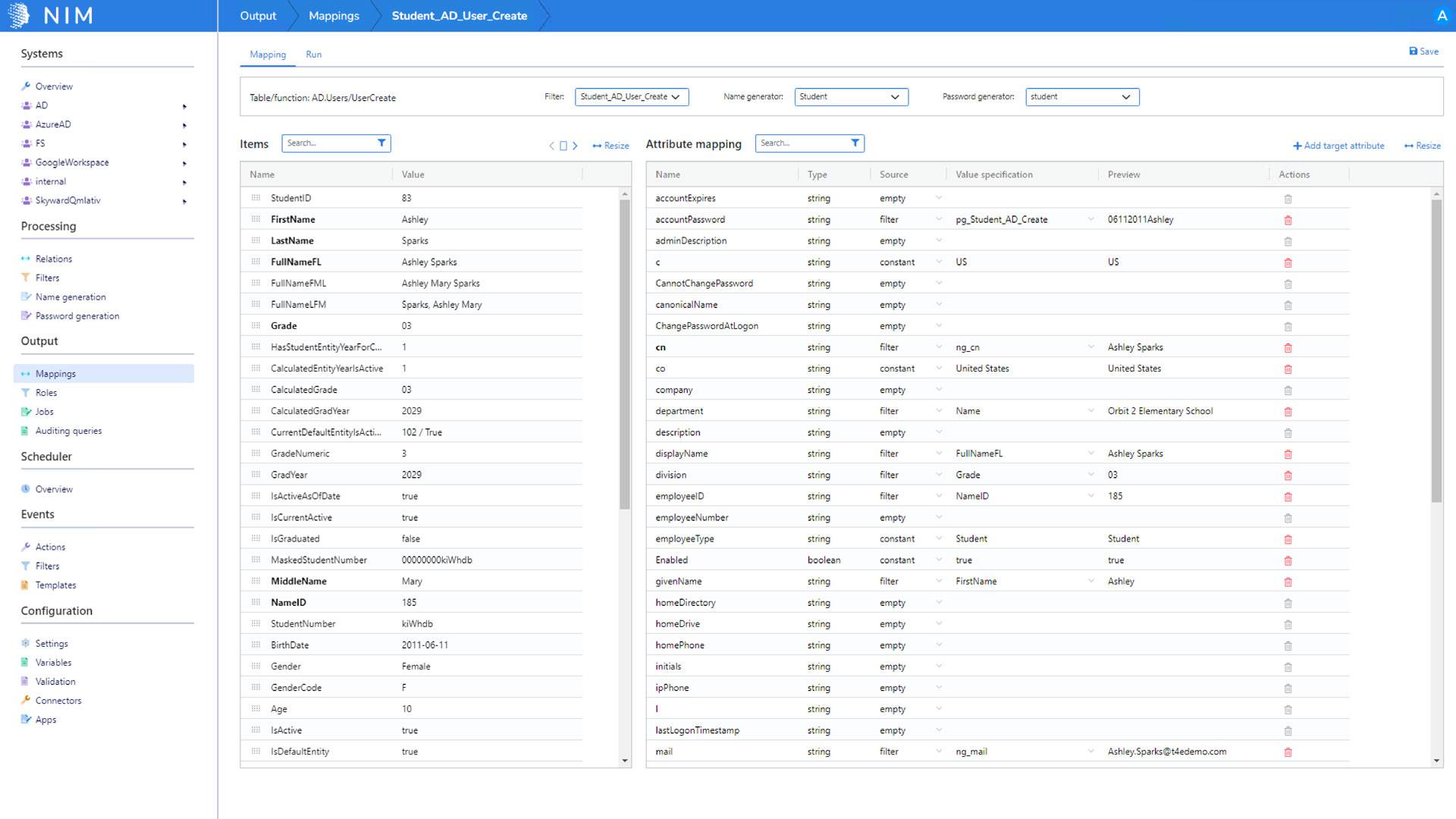
With NIM’s optimized provisioning engine, targeted data mapping profiles, and advanced scheduling, user lifecycle management takes minutes instead of days, no matter the number of users or systems. Easy to configure lifecycle processes to automate user provisioning directly to a target system.
Secure Onboarding
NIM’s onboarding process offers new users a seamless and secure way to claim their accounts. Upon successful verification, users are provided with their username and the option to set a new password, ensuring a smooth and secure account-claiming experience.
Self-Service Password Reset
NIM’s Self-Service Password Reset feature empowers users to securely reset their passwords across multiple systems once their identity has been verified. This streamlined process enhances user autonomy and security, making password management hassle-free and efficient.
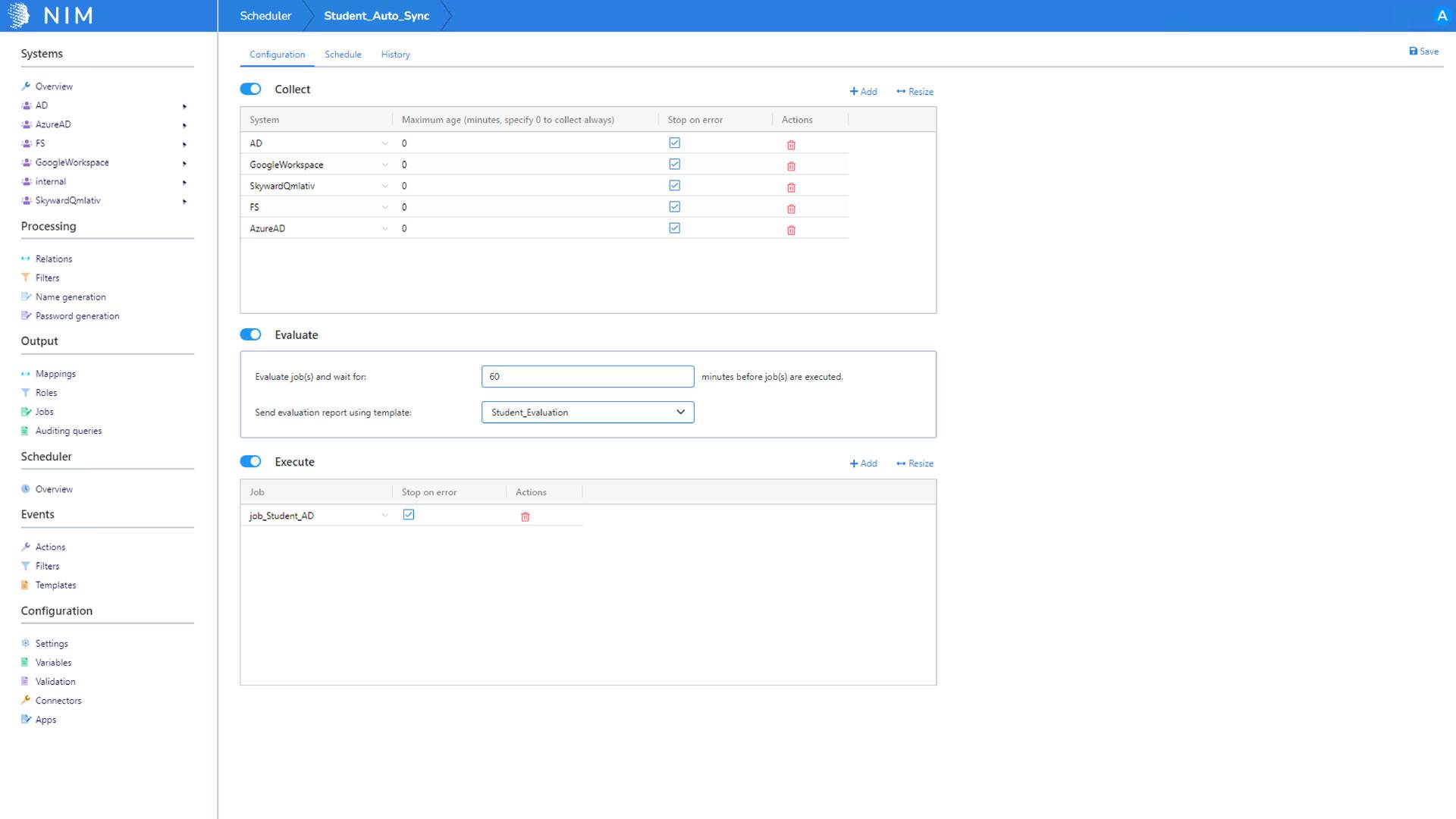
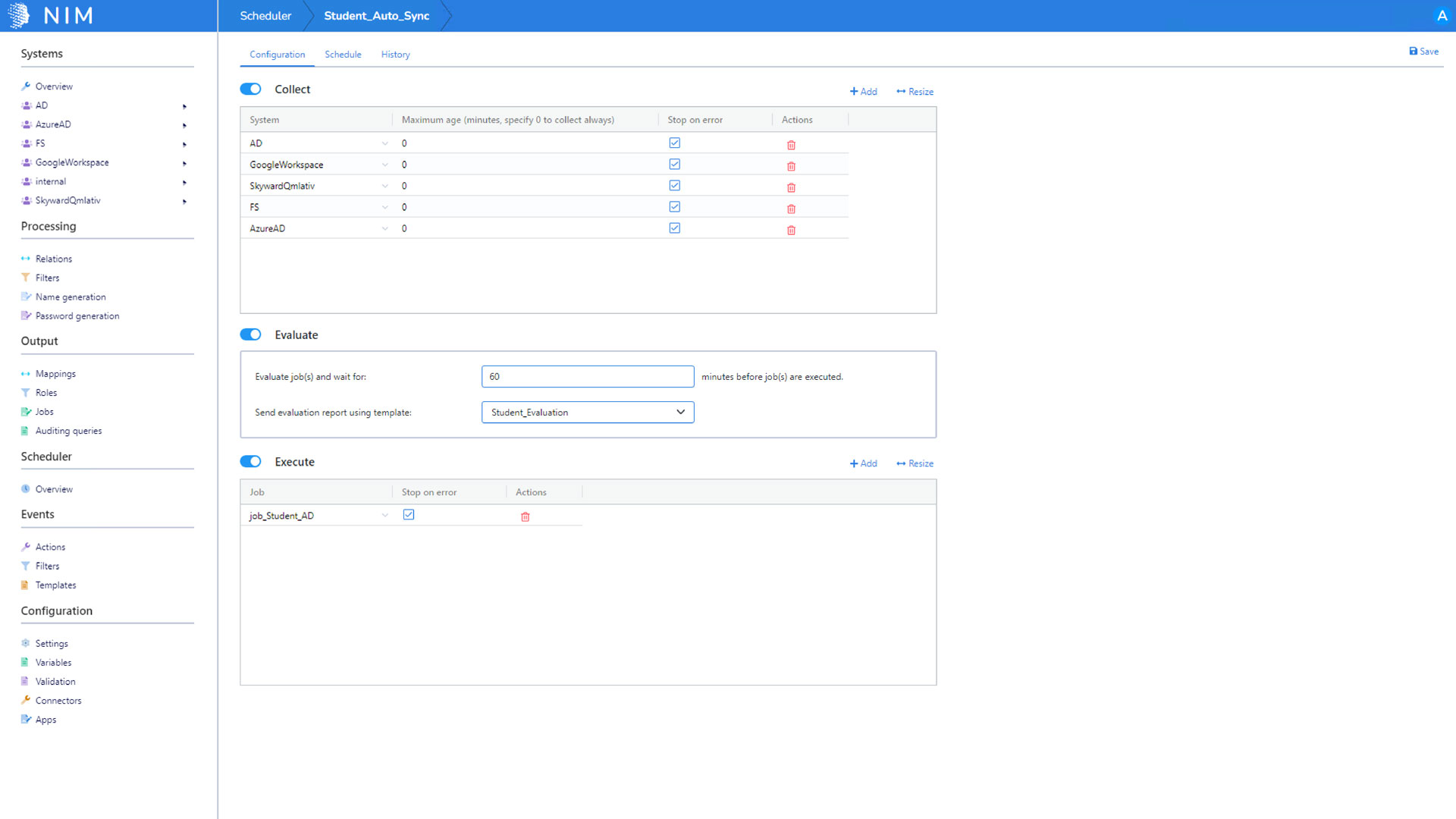
Flexible Scheduling
With NIM’s advanced scheduling, you can control when data is collected at an individual system level. Reduce the time between data collections by focusing on the systems with more frequent data updates.
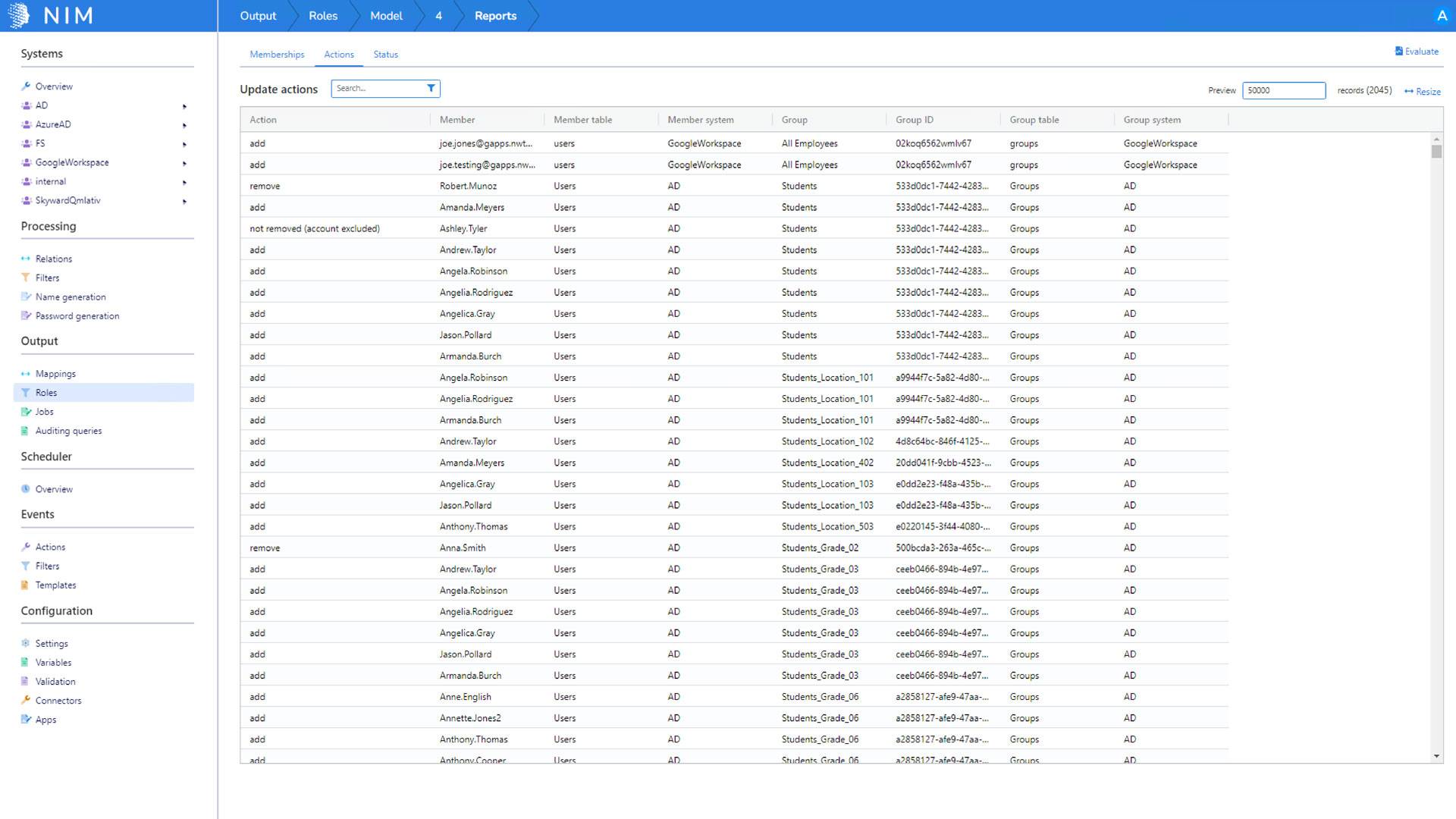
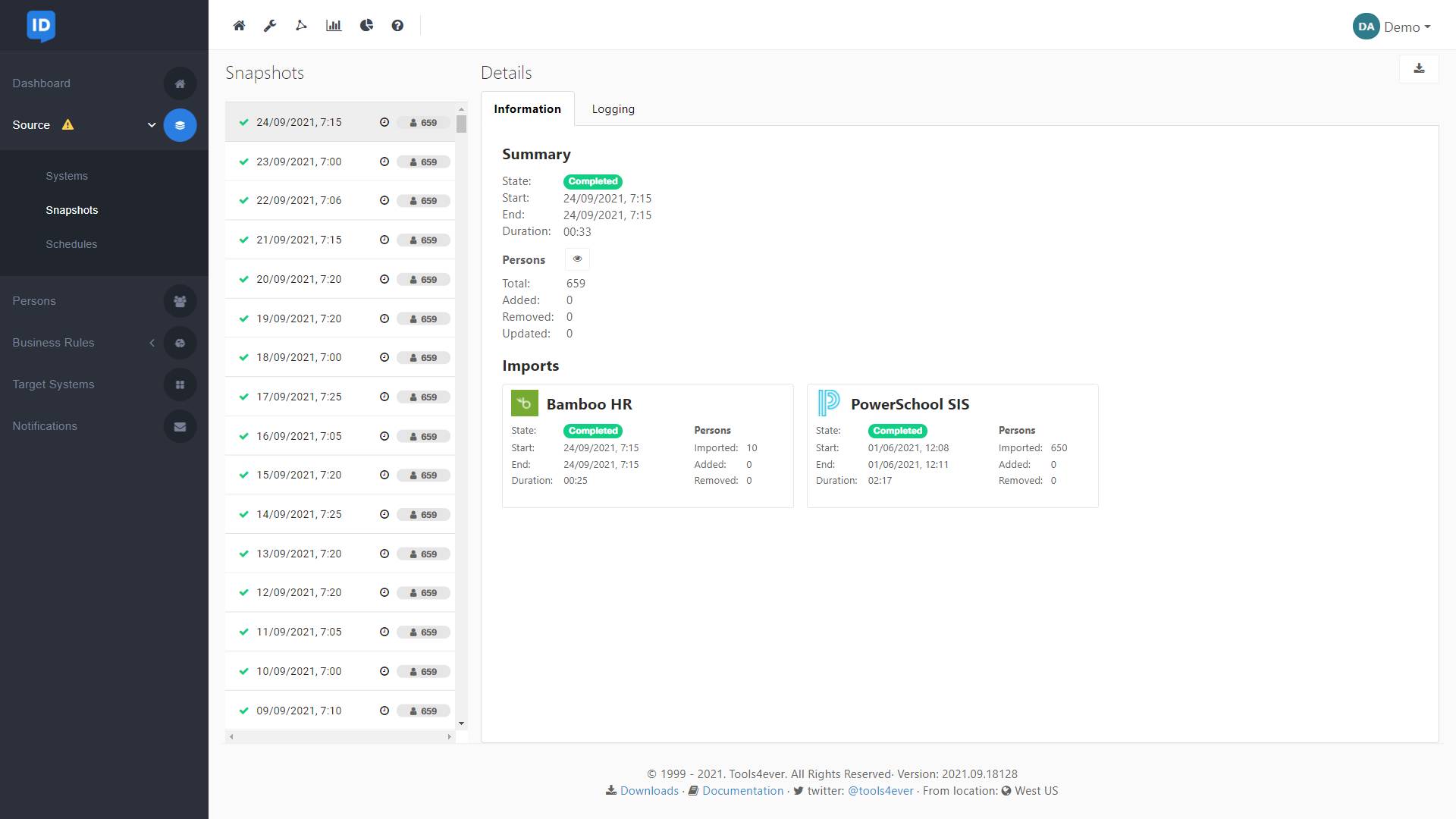
Impact Analysis & Audit Reports
Audits have never been easier, thanks to NIM’s enforcement reports and detailed evaluation feature that allows for real-time impact analysis before any user provisioning action is committed.
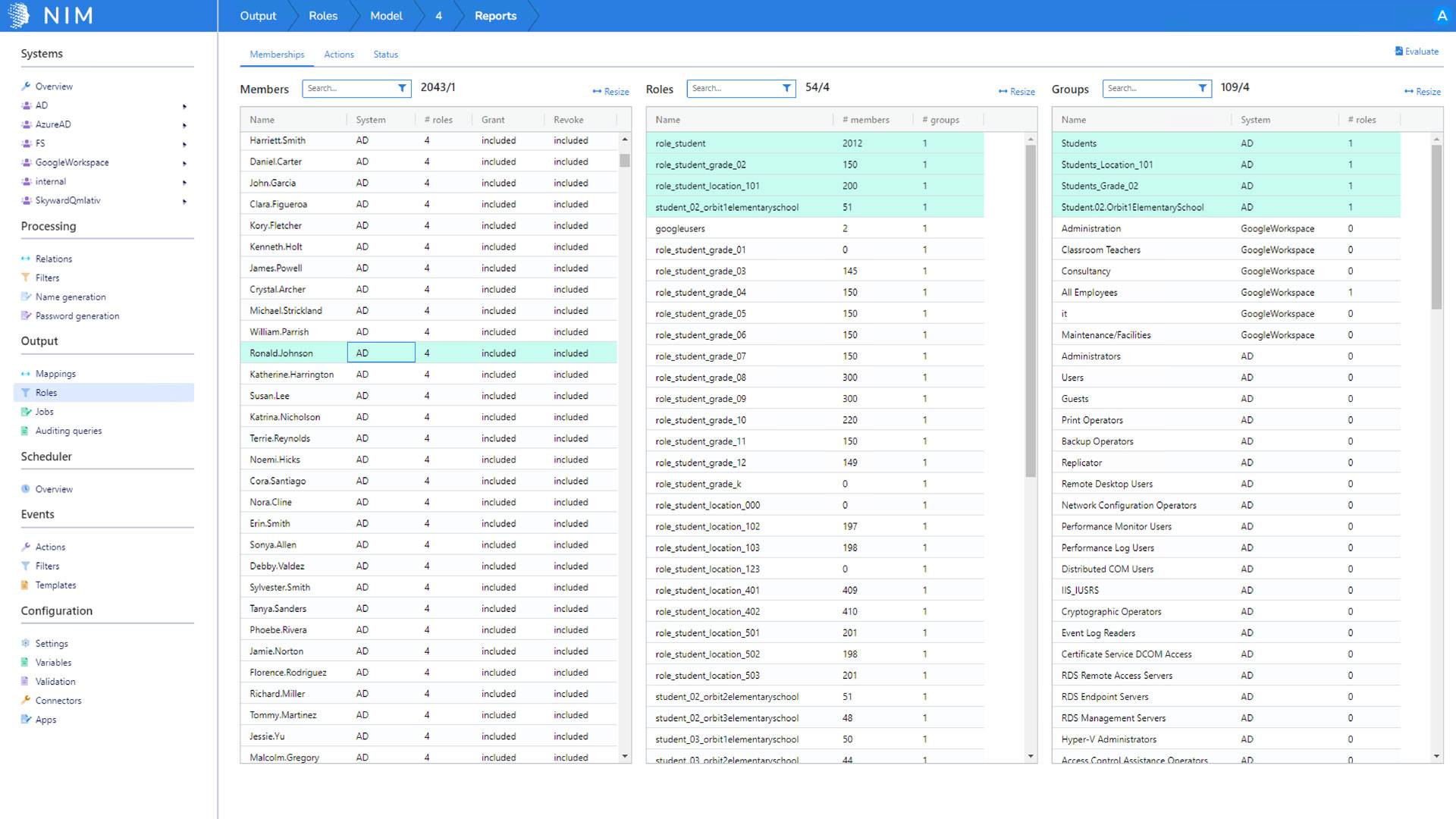
Role Modeling
Create thousands of business roles in minutes using NIM’s simple-to-use Role Mining feature. Detailed analysis of Users, Groups, and Roles across your systems with a single click of a button.
Data Exports & Rostering
Provisioning is the goal, but data is king. With NIM’s unique multi-source and target data aggregation features, data from multiple systems can be viewed and utilized for provisioning, rostering, and basic exports. Simply use NIM’s advanced filtering to combine data from multiple systems to generate customer exports to import into 3rd party systems.
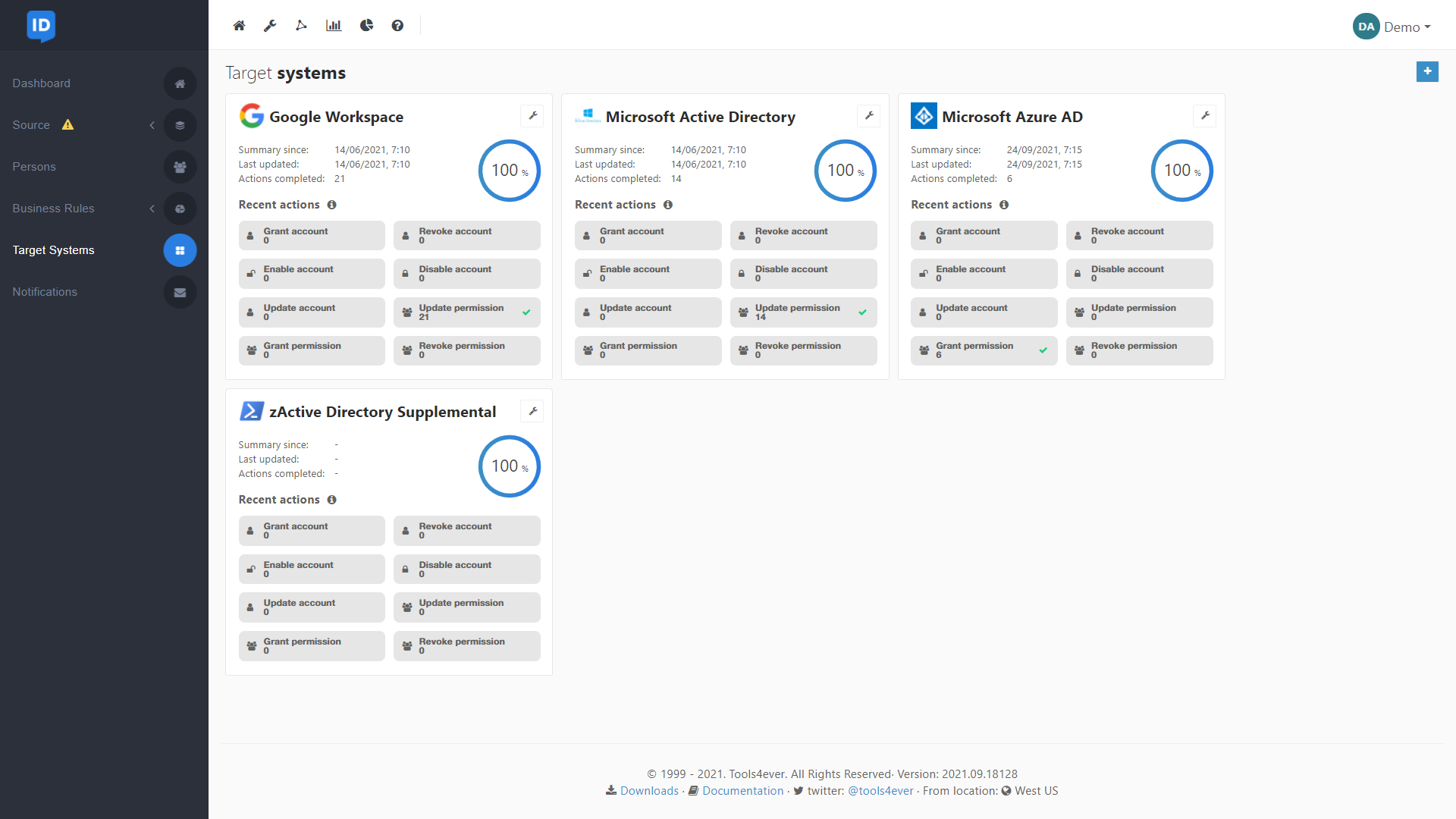
Source & Target Systems
Data comes in all types of formats. NIM asynchronously collects all data and loads it into memory for easy internal access and increased performance. Additionally, historical collection data is readily available for delta comparisons. NIM’s internal historical data management allows for simple rollbacks if the situation requires it.
Connector Management
NIM simplifies the process of upgrading system connectors, allowing users to update to the latest versions with a simple press of the “Upgrade” button, which automatically downloads the newest connectors from NIM’s GitHub repository. This feature ensures that users always have access to the most current and secure connectors with minimal effort.
Open Data Model & Architecture
NIM supports an open data model and architecture that leads to a flexible solution that meets many of your organization’s identity management needs.
Custom Apps
Design helpdesk and organization Apps tailored to meet all your needs using NIM data. Apps are the perfect way to delegate responsibilities securely with auditing and streamlined functionality.
Data Accuracy
Automated User Provisioning allows for enhanced data accuracy by removing human error, which can unknowingly cause access permission issues or misspellings.
Better Decisions, Better Results
NIM’s unique approach to “Data-Driven Decision Making” empowers IT departments to design and manage their user provisioning processes without scripts or costly consultancy services.
While straightforward configuration is paramount, visibility is key to easy management. What is visibility? It’s the ability to see Current, Future, and Historical actions/attributes from all source and target systems in a single view from a group level down to an individual user account.
Key Features
High ROI with Low Lifecycle Replacement
Open Data Model Supporting Simple to Complex Implementations
Integrated with Top HR & SIS Solutions
Community Driven Feedback
Single Source of Truth (Soll-Ist) Capabilities
Data Warehouse with Detailed Source & Target Relationships
Unlimited Number of Users
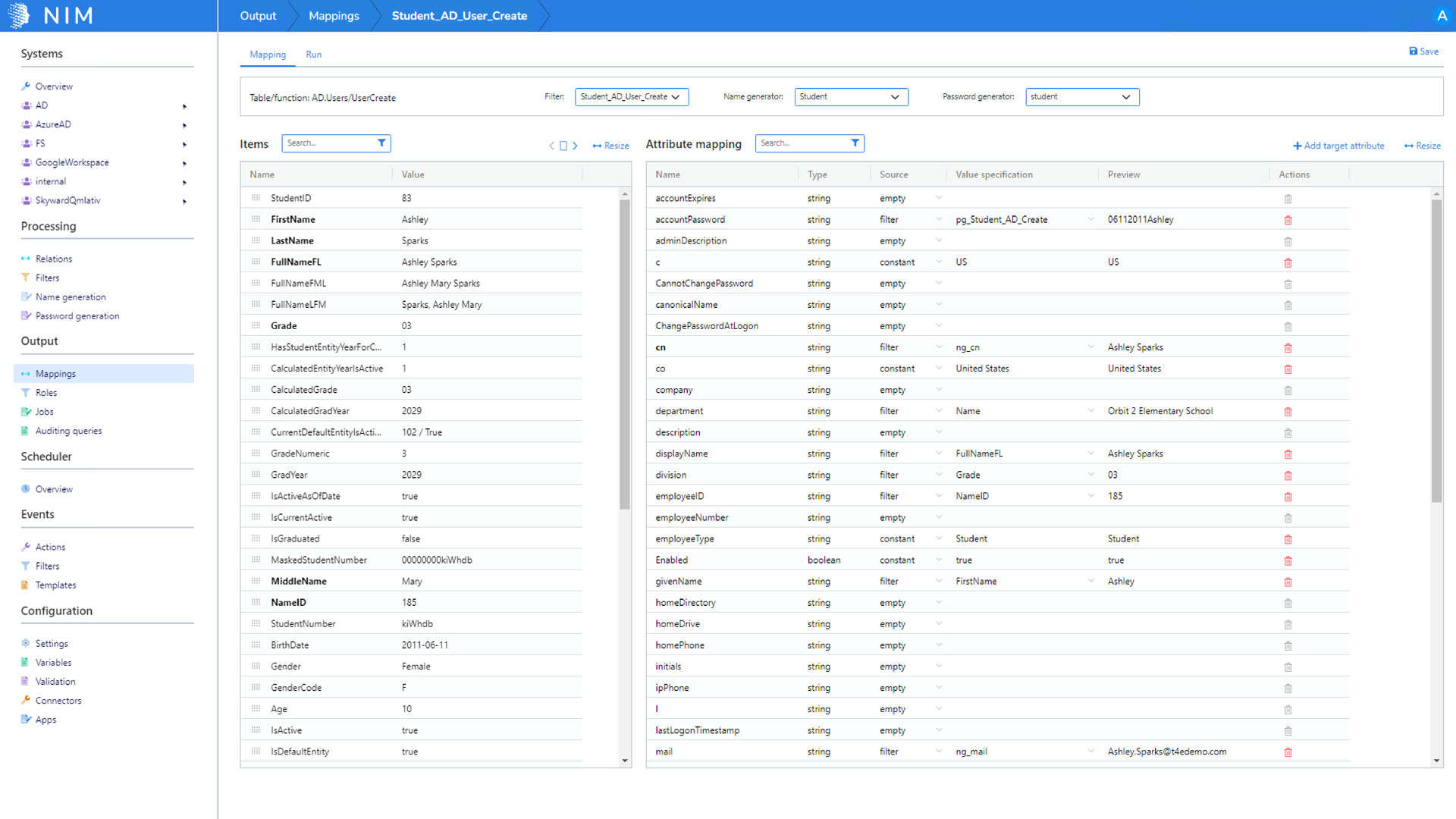
Granular Name Generation
Secure New User Onboarding
Tailor-made Reports (including Notifications and Web Applications)
Detailed Impact Analysis (Know Before)
Unlimited Data Synchronizations per Day
Self-Service Password Reset
Customizable HelpDesk & Organization Web Applications
Advanced Audit Logging and Query Capability
No Additional Software Needed

Enterprise Capabilities Without the Price Shock
NIM is an on-premise tool that provides enterprise-level user provisioning capabilities for organizations looking for a flexible solution. With NIM, you can provision users in a matter of minutes and track changes throughout the entire process.
As a specialized user provisioning tool for enterprises, it is optimized for performance and easy self-management for any size organization with complex multi-system environments, including multiple data sources and targets.
Its simple menu-driven functionality allows you to filter data quickly, view impact analysis reports, and execute targeted lifecycle management across unlimited systems and exports with no scripting knowledge needed.
NIM supports an unlimited number of source and target systems such as Active Directory, Azure AD, Google Workspace, UKG UltiPro, Oracle, and Office 365.

Performance and Easy Self-Management
- Create, Modify, and Assign Users to Groups and Roles within minutes via NIM’s Intuitive Interface.
- Make the most of your data by utilizing cross-platform data analysis and filtering.
- Manage security by leveraging NIM’s advanced roles and group management.
- Leverage Detailed Logging, Generate Impact Analysis Reports, and Create an Audit Trail with ease.

Optimized for Performance and Ease of Use

When Performance Matters, NIM Delivers
This quick guide will help explain how NIM can maximize user efficiency, increase the organization’s security, and free up IT resources.
Lifecycle management or user provisioning is the process of creating, editing, and disabling user accounts in an organization. It can be done manually, or the process could be automated using specialized software like NIM. Automating the provisioning process aims to increase security, reduce errors and allow IT to concentrate on more impactful projects.
The most common use case for user provisioning or onboarding is when a new person joins the organization. They will need an email address and access to specific resources, depending on their role. These resources can be spread across multiple platforms, both internally and externally.
Additionally, user updates and offboarding are vital security concerns. For example, when an employee changes roles or leaves an organization, IT departments need to manually adjust or remove permissions. An automated system reduces these security concerns when a properly configured Role-Based-Access-Control (RBAC) solution, such as NIM, is implemented.

Efficient Automated User Provisioning
Manual user provisioning is tedious and time-consuming. You have to wait for someone to complete all the forms and answer all the questions before you can create their login credentials and set permissions in multiple systems. Not only do you have to wait, but you also have to remember to notify HR and managers of the new accounts so they can properly onboard the new employee.
If you’re looking for a solution that will automate the entire process, look no further than NIM. NIM streamlines the process by allowing you to quickly create new users and assign them the right permissions. As a result, what used to take days can now be achieved within minutes.
NIM is particularly easy to set up in your organization thanks to no scripting knowledge needed and its out-of-the-box source and target connectors, such as Active Directory, Microsoft Azure AD, Google Apps for Work, Salesforce, Office 365, and others.

The Three Pillars of Identity Management
Identity management is built on three important pillars, all designed around your organization’s digital identities: Automation, Security, and Auditing.
Automation ensures that the right person gets the right accounts, memberships, and information at the right time. For new employees, movers within the organization, and leavers, the changes in their digital identities are made in time and when needed.
Security is one of the biggest challenges for organizations. It’s a tight balancing act to ensure that employees have the right amount of access without compromising your organization’s security. Therefore, detailed role modeling using multi-system data evaluation is a cornerstone in creating an automated user lifecycle management solution with security as the focus.
Auditing is essential. When manually performing all changes and actions for every digital identity, an audit is costly and time-consuming. SOC2, ISO27001, and other compliance certifications are very important to ensure that data within an organization is handled correctly and that access is limited to where it is needed.
NIM’s unique design and open data model make it extremely flexible, allowing NIM to meet more of your organization’s identity requirements and integrate into your existing infrastructure. Therefore, current manual tasks can be automated and enhanced with detailed auditing. Additionally, NIM’s advanced features, such as role modeling, customized audit queries, and scheduled reports, help organizations grow their digital infrastructure in a manageable and secure way.
Identity management is a complex problem requiring a sophisticated solution. With NIM, a true user lifecycle management solution can be designed by creating relationships between source and target systems, therefore, enriching your own data.
As your needs evolve, so does NIM, designed for performance and easy self-management.
NIM FAQs
Does NIM require a SQL license or additional database software?
No, NIM uses an internal SQLite database and does not require an external database. However, NIM can connect to a SQL database as a source or target system.
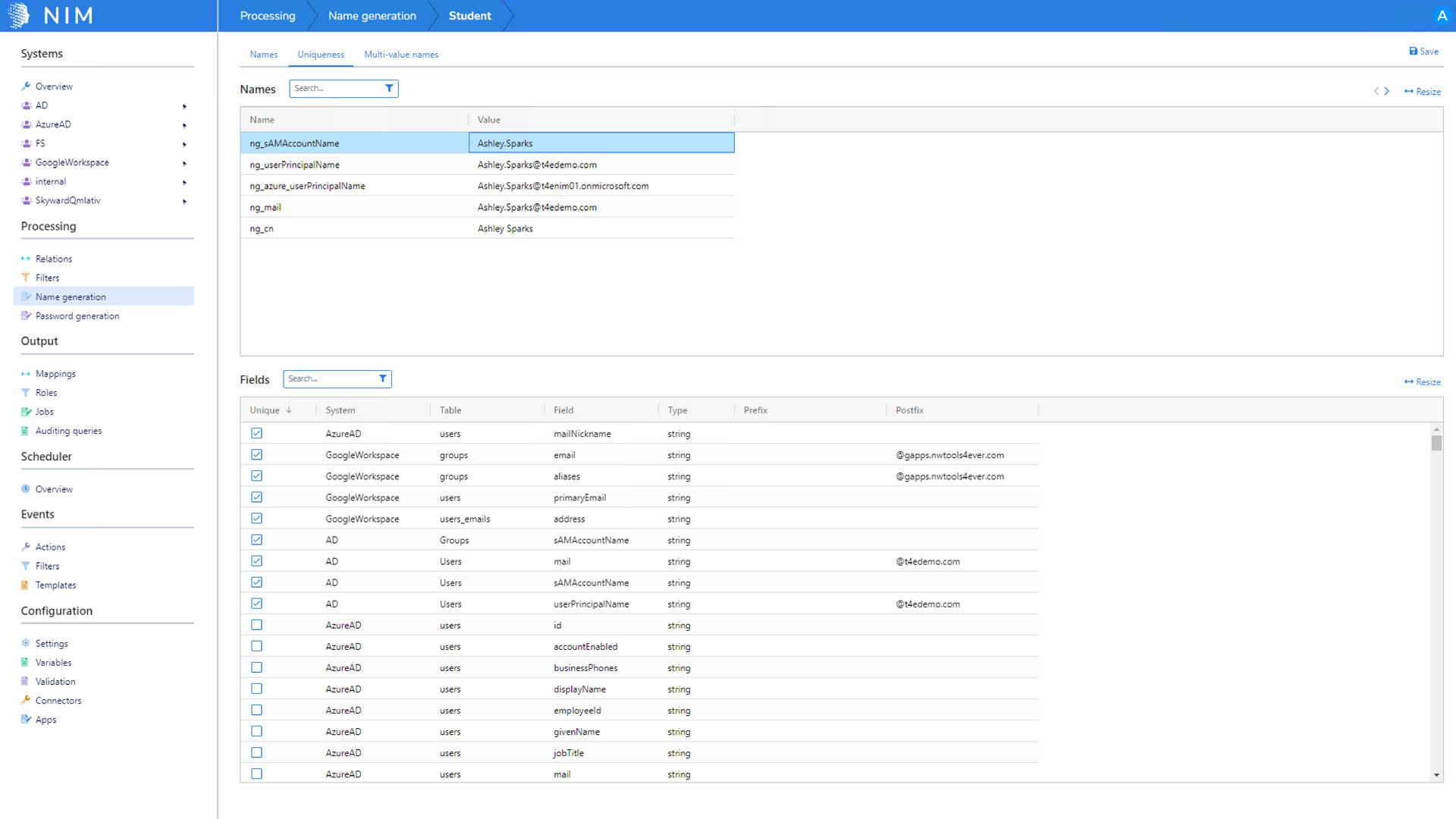
How does NIM handle full name, username, and email uniqueness?
A true identity management solution should never lock you into a specific name generation algorithm. NIM is designed to allow you to control the entire name generation process. A major part of that process is uniqueness. NIM has an entire section dedicated to uniqueness requirements. Typically, "uniqueness" is evaluated for full name, user name, and email, but in reality, it can be used for any generated variable within the NIM "Name Generator" process. Uniqueness requirements can be designed to evaluate all target systems for uniqueness before the variable is generated.
For example, guaranteeing the username is the same across all target systems. If NIM's Name Generator determines a downstream target system has a user name duplication conflict, the generator will iterate to a new username and reevaluate all target systems for uniqueness. The iteration algorithm is extremely flexible, which makes it easy to configure to meet your organization's requirements.
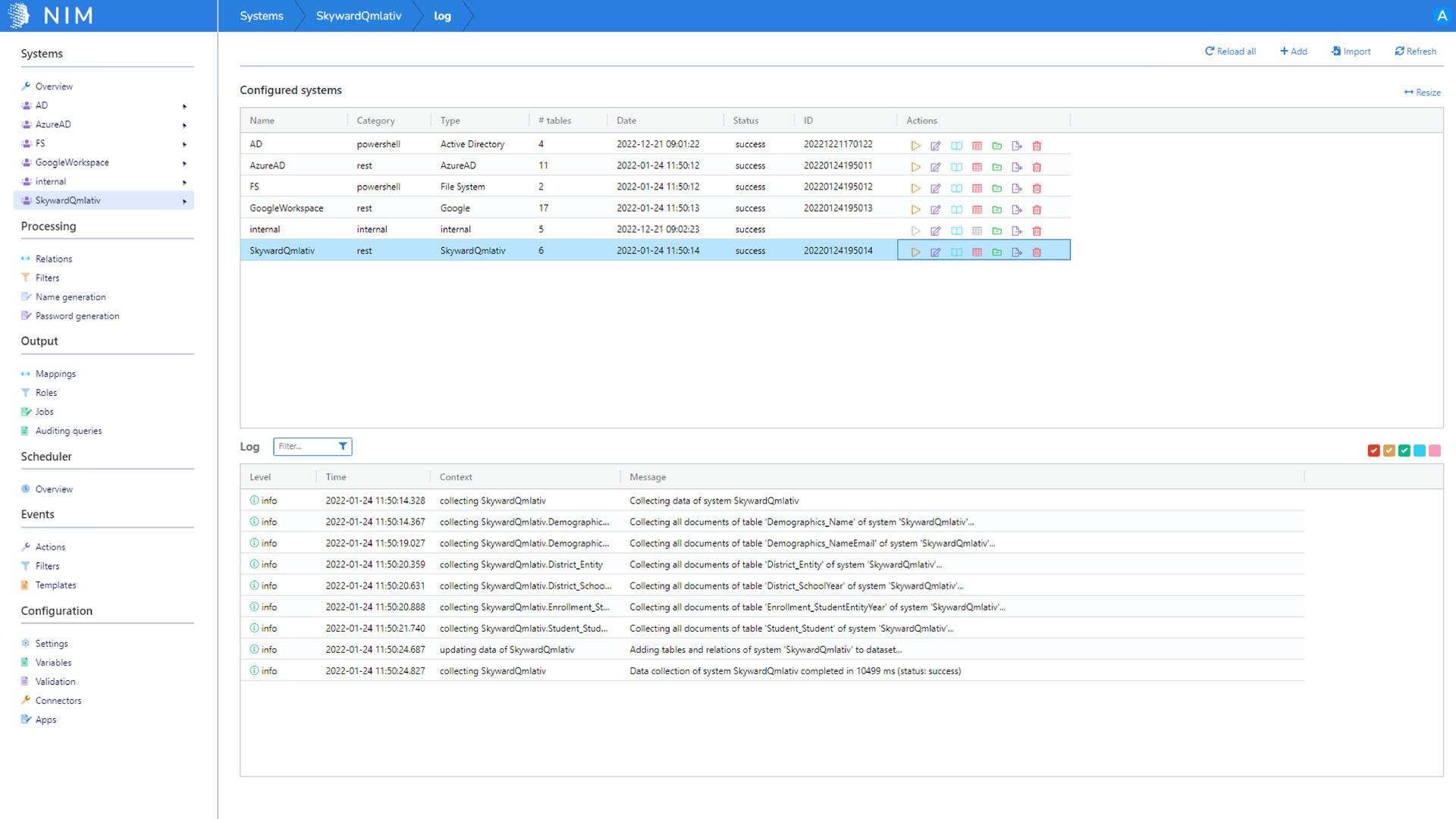
How many source and target systems does NIM support?
NIM's open data model is designed for simple to complex multi-system environments. This allows NIM to support virtually an unlimited number of source and target systems.
Some common systems are UKG Pro, Workday, BambooHR, Active Directory, Azure AD, Google Workspace, SAP SuccessFactors, Dropbox, ADP, and Salesforce.
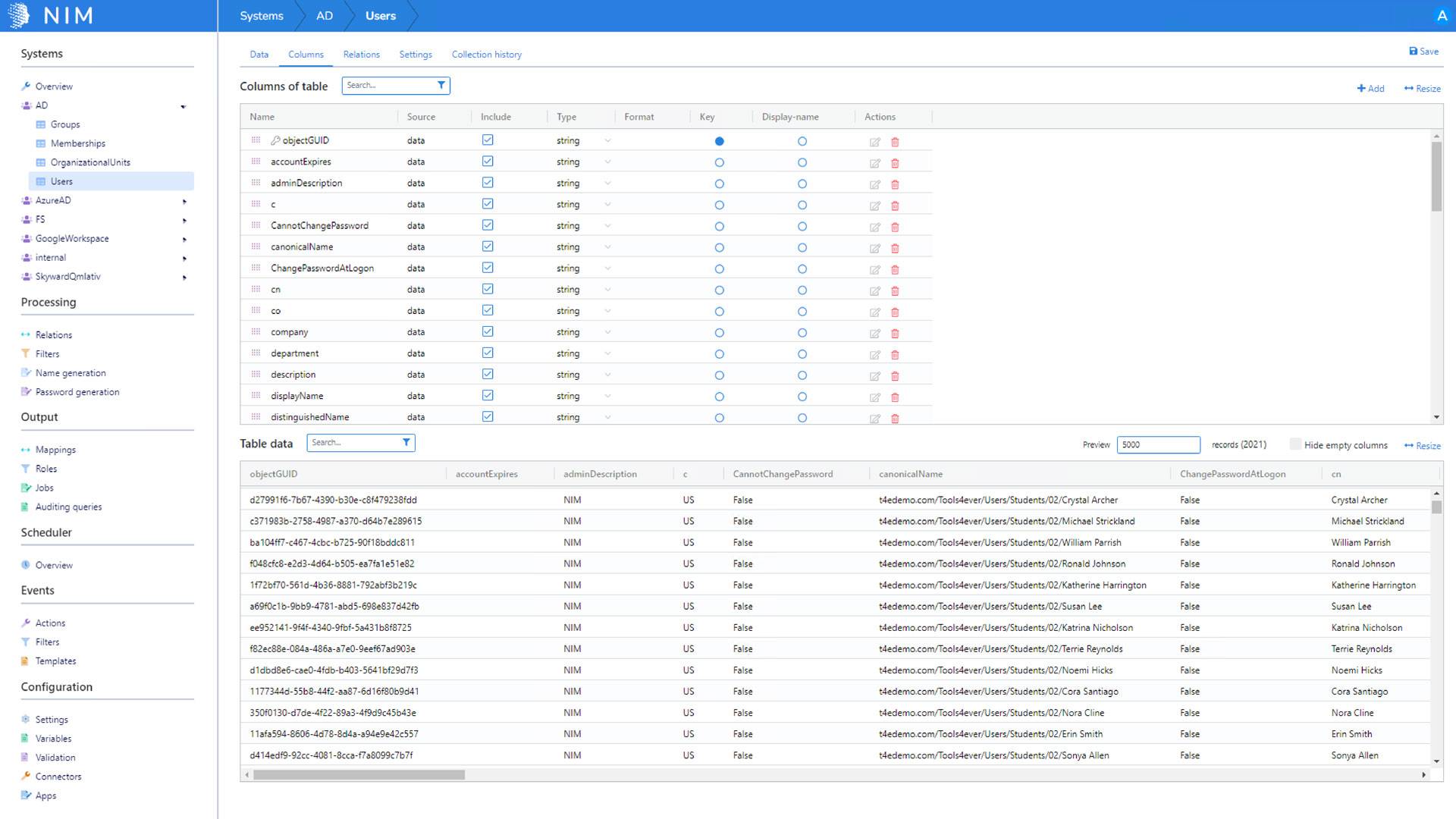
How many user identities does NIM support?
Unlimited, NIM's core design is to support small to extremely large (200K+ identities) without sacrificing performance. This is accomplished by using the host system's memory and optimized data relationship algorithms.
What are NIM Applications?
NIM's main focus is automating an organization's user lifecycle provisioning process. However, not everything can be automated, and manual processes are required. This is where NIM Applications come into play. Organizations can customize web applications that leverage NIM's data and internal processes, such as data relationships, role models, and name and password generation. In addition, each application has its own security access control list (ACL). This allows you to delegate applications to specific roles, such as the Helpdesk or a single user. All the while, it logs every action to be used for auditing purposes.
Below is a list of possible NIM Applications:
- Creating non-HR related user accounts such as temp workers or substitute teachers
- Helpdesk ad hoc group management
- Teacher classroom student password reset
- AUP and Acknowledgement form
- List Users Created or Modified past 30 days
- List Users with password Expires within a timeframe
- List users with no logon in the past X days
Does NIM require scripting knowledge such as PowerShell or JavaScript?
No, NIM is a menu-driven identity management (IDM) solution that does not require scripting knowledge. However, NIM supports advanced features such as using JavaScript to generate new data columns based on existing columns or manipulating the data format of a column when required.
What is NIM Role Modeling?
NIM's Role Modeling feature allows you to create business roles to help manage entitlements. An example of entitlement is an Active Directory security group or distribution group. Roles are typically based on filtered information such as job title, building location, etc. In addition to role management, NIM supports role mining and role generation.
Role mining is where you analyze your current group configuration across all your systems and display commonalities. For example, the job titles "marketing assistant" and "marketing supervisor" are members of the same five marketing groups.
Role generation is where you use role mining information to generate roles. For example, one role for marketing includes two job titles, "marketing assistant" and "marketing supervisor"; the entitlements are five groups.
Where can I find more information on configuring NIM?
For detailed information on how to configure NIM, such as source and target system configuration, user name and password generation, OneRoster exports, role mining, role generation, and much more, visit our NIM documentation website at https://docs.nimsuite.com/
What is synchronization vs. event-based evaluation?
Tools4ever has two provisioning products, NIM and HelloID, that utilize two different methods of evaluating source data: synchronization and event-based evaluation.
NIM uses a synchronization method based on the "soll-ist" philosophy of "desired situation" and "current situation." This method is also known as a "Single Source of Truth," where source data is synchronized to downstream systems on a schedule. NIM accomplishes this by evaluating the data from all source and target systems. When NIM identifies data in the target systems that does not match the source system, NIM will synchronize the source data to the target system. This method guarantees that all downstream systems have the same information as the source system.
HelloID uses an event-based evaluation method. On schedule, source data is evaluated for changes. When a change is detected, that change will then be propagated to downstream systems. In this method, downstream systems may contain different information than the source system. This allows for ad hoc changes to downstream systems without the worry that the source system data will overwrite the ad hoc change.
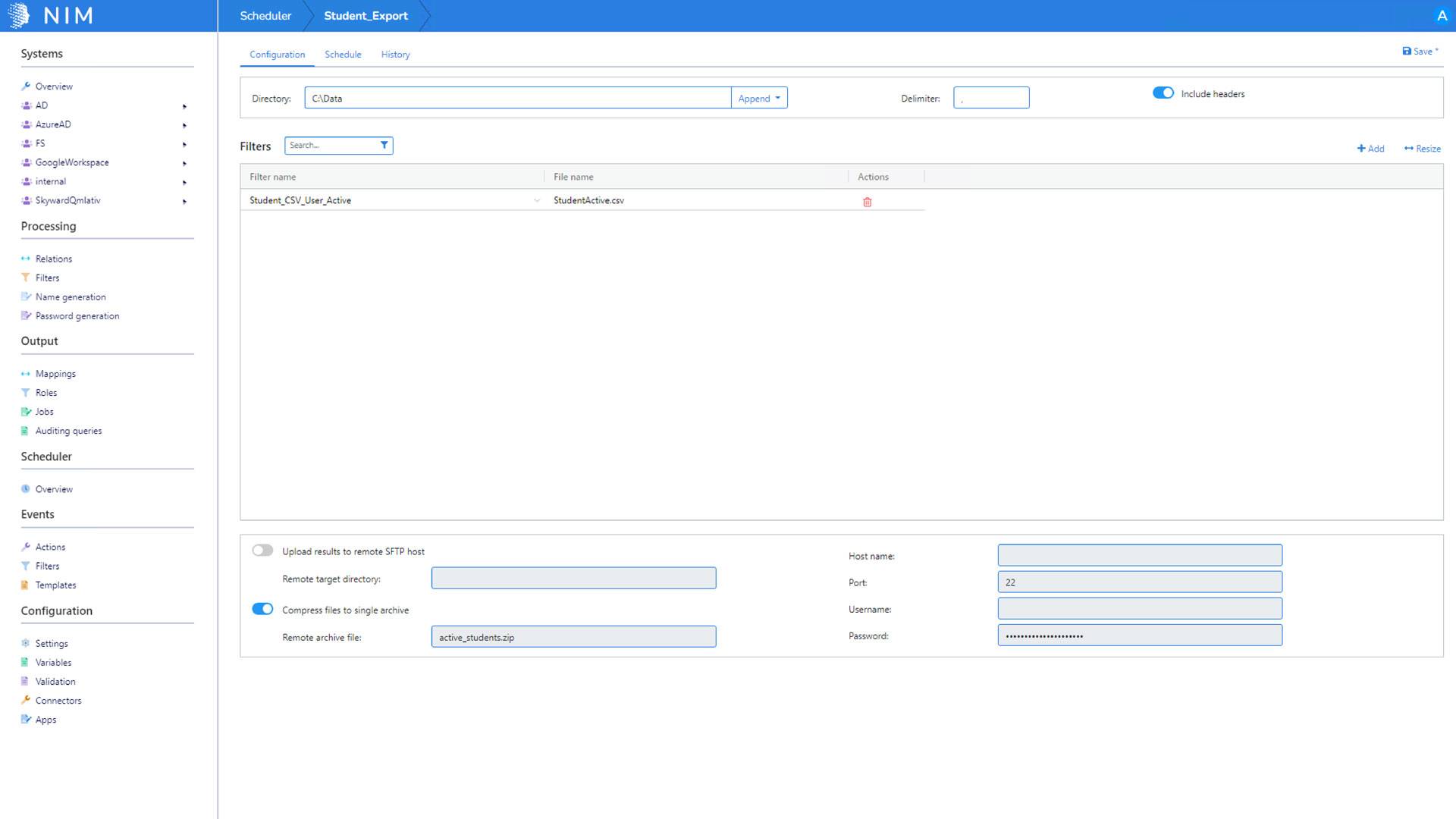
Does NIM support SFTP?
Yes, NIM's export functionality can also be configured to execute SFTP transfers. This allows NIM to not only export a file or multiple files (typically CSV) but can also transfer the file to a target system using SFTP. Additionally, in compliance with the OneRoster specification, you can compress the files into a single zip before uploading as well.
Can we have separate password generation algorithms for elementary and everyone else?
Yes, NIM supports any number of "Password Generators." For example, it's not uncommon for school districts to generate simple passwords for Pre-K and Elementary students. Typically these passwords use information found within the Student Information System (SIS). With NIM's multiple password generator feature, NIM can integrate into your current identity management infrastructure with minimal effort.