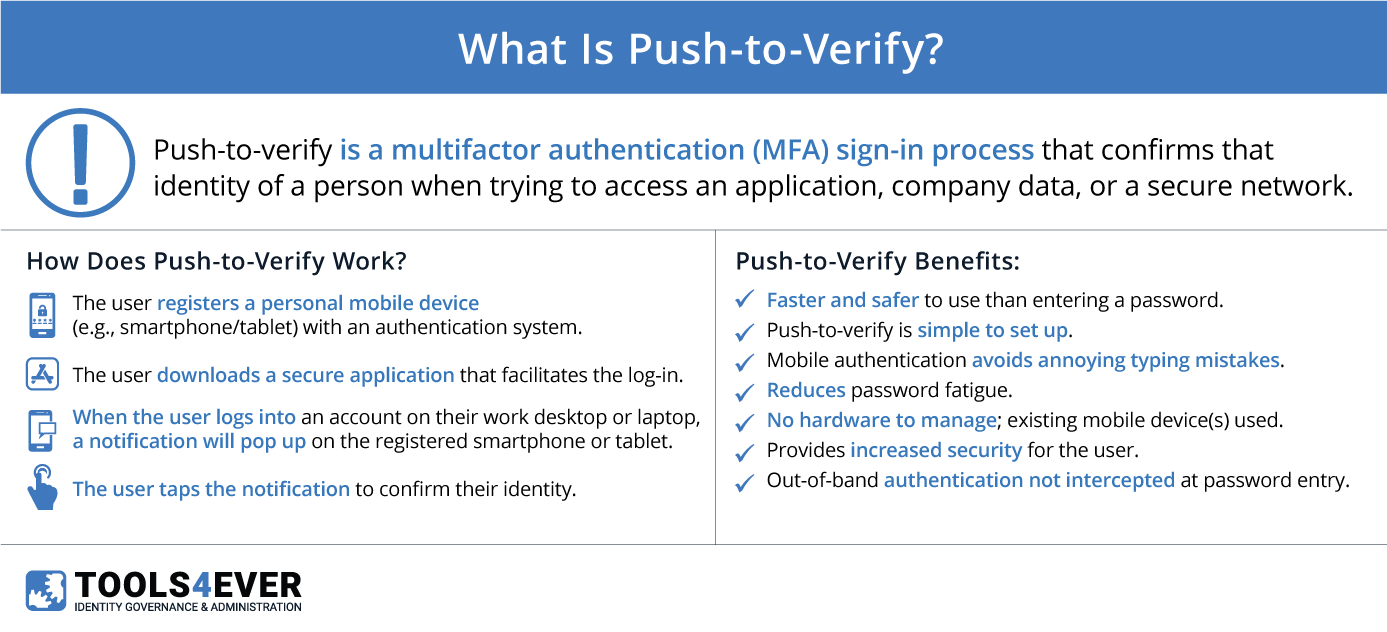
Identity matters. Before gaining access to an application, company data, or a secure network, the identity of the person must first be confirmed. Many apps and networks use a multifactor authentication (MFA) sign-in process known as “push-to-verify” to accomplish this feat.
Push-to-verify, or push notification authentication, works like this:
- A user registers a device they possess, such as a smartphone or a tablet, with an authentication system.
- The user downloads a secure application that facilitates the login. Doing so links the user’s device to the server.
- When the user logs into an account on their work desktop or laptop, a notification will pop up on the registered smartphone or tablet.
- The user taps the notification, confirming their identity, and is authenticated.
For many multifactor authentication processes, the first step remains traditional username and password credentials but other options exist. Push-to-verify often follows this initial authentication. Rather than entering a password, the system sends a push notification directly to the secure application on the user’s registered device. The notification prompts the user to approve or deny the request. With a single tap, the user then acknowledges receiving the notification through the app and gains access to the secure network.
If there is a situation where the user denies the request, an administrator can be immediately alerted so that they can take any necessary action to secure the data.
Push-to-verify is one of the fastest-growing authentication factors available. Half of the enterprises using mobile authentication likely have adopted push to verify as their authentication method of choice.
Advantages & Security
Push-to-verify provides several benefits for users:
- Faster and safer to use than entering a password.
- Push-to-verify is simple to set up.
- Mobile authentication avoids annoying typing mistakes.
- Reduces password fatigue.
- No hardware to manage; existing mobile device(s) used.
- Provides increased security for the user.
- Out-of-band authentication is not intercepted at password entry.
Anyone that has tried to remember a complicated password or fumbled to open their password storage app on their phone understands that validating an authentication request is much quicker than typing. Through push notifications, the user is freed from remembering a myriad of passwords, allowing them to focus on the important tasks they have to accomplish.
When compared to other multifactor authentication options, push verification offers robust security and the ability to deploy with minimal hassle for end users. Push-to-verify is especially simple when compared with other options, such as security questions, additional passwords, or one-time passcodes.
Eliminating Weak Passwords
Push-to-verify helps eliminate the risk of weak passwords (Password123). Complexity requirements help, but if users are left to determine their own passwords, they may still choose easily guessed credentials. By adding an additional authentication layer, you enforce a secondary safeguard to drastically mitigate the vulnerability of any weak passwords that might still be used.
Push-to-verify uses what is known as “out-of-band authentication”. Out-of-band authentication (OOBA) is a process where authentication requires two different signals from two various networks or channels. These kinds of more sophisticated authentication prevent many types of fraud and hacking.
OOBA effectively blocks many of the most common kinds of hacking and identity theft in online banking. This is because OOBA requires an attacker to breach two communication channels rather than one, providing more security than other authentication methods. Communications are encrypted between the application and a secured authentication service.
Reduced Helpdesk Calls
Particularly when combined with Single Sign-On (SSO), an unsung benefit of push-to-verify is a reduction in calls to the helpdesk related to resetting passwords. If a user only has to remember one set of credentials, this substantially helps fight “password fatigue”, or the challenges associated with remembering many complex passwords. Paired with SSO, push-to-verify MFA both increases security and eliminates the need to remember credentials for additional systems and resources.
The result is fewer expenses, as your IT department no longer has to manage these trivial reset tasks. Push-to-verify increases productivity across the organization, allowing your employees to gain access to their resources quickly and securely.
Less Hardware
Push authentication typically incorporates into a user’s smartphone, so there are no additional hardware requirements. There is no need for any IT department resources, as users can simply download and install the app. Many push-to-verify apps are free.
Vulnerabilities
Push-to-verify possesses some weaknesses. The device, for one, is a factor for unreliability. As the user is not required to enter a password (they only accept the notification on their device), the hacker has access to the secure network if the device is stolen and compromised. Many data breaches have come as a result of stolen property.
Another potential security issue is if users inadvertently approve a fraudulent request. If a user receives many notifications in short order, they may click “approve” without looking too closely at the notification.
There are ways to reduce the likelihood of this occurring, however. Many organizations provide a review service, where a notification is sent to the user if unusual log-in attempts or account activity is noted. In these instances, the notification has a specific request ID that the user must match to approve the request.
Push-to-Verify: MFA for the Future
As more companies adopt a push-to-verify model, they are building on successful examples from companies, such as Salesforce, Twitter, and others. These companies offer a push-to-verify log-in option for users, usually in conjunction with an authentication app.
Tools4ever’s push-to-verify feature, the HelloID Authenticator App, is available for both Android and IOS systems. With the HelloID Authenticator App, users can seamlessly verify their identity with a single tap.
As data security becomes more critical and hackers more skilled, the need to offer reliable, secure access is crucial to a business’s success. Push notification authentication offers that security in a cost-efficient manner. Push-to-verify is one of the fastest-growing authentication factors available and is becoming a staple in many organizations’ authentication processes.
Please check out our documentation site for an easy, step-by-step tutorial on the HelloID Authenticator App.
