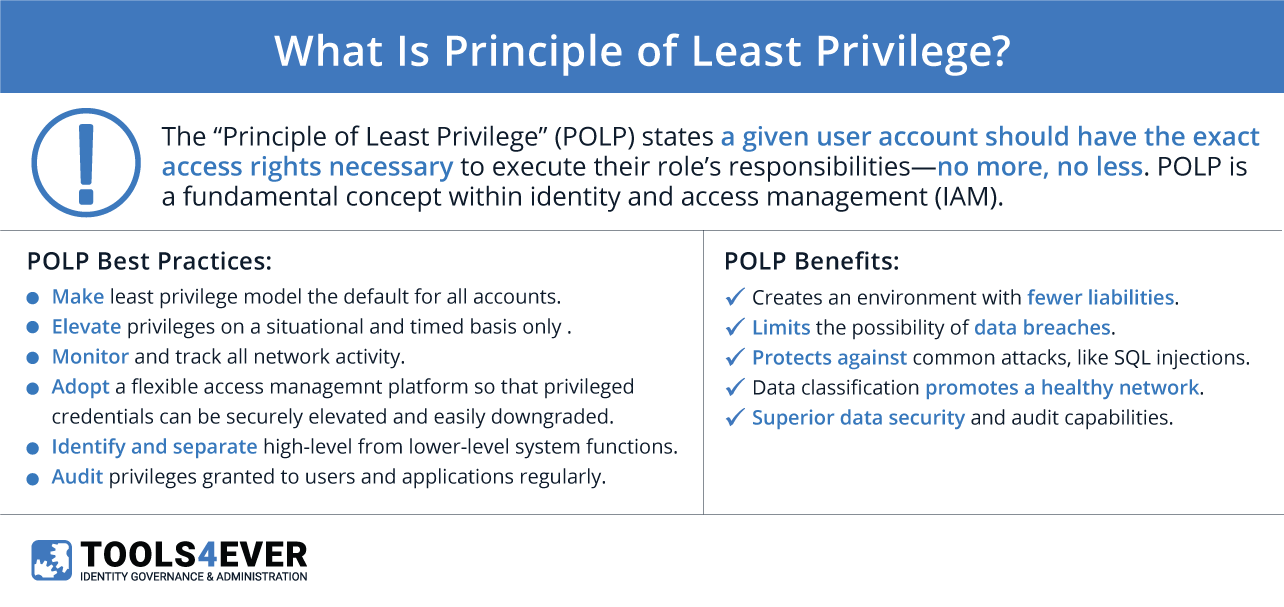
The “Principle of Least Privilege” (POLP) states a given user account should have the exact access rights necessary to execute their role’s responsibilities—no more, no less. POLP is a fundamental concept within identity and access management (IAM).
Least privilege relies on the understanding that pragmatic access straddles a balance. An employee can’t complete their job without the minimum access requirements, yet too much creates compliance and security risks. Least privilege is critical for preventing the continual collection of unchecked access rights over a user account’s lifecycle. The “user account lifecycle” defines the collective management stages for every user account over time—creation, review/update, and deactivation (CRUD).
This gradual accumulation is colloquially referred to as “privilege creep”, “access creep”, or “permission bloat”. These information security vulnerabilities most often coincide with promotions, role changes, reassignments, or comprehensive reorganizations. The dangers of access accumulation extend beyond employees, however, with service accounts. Service accounts are special user accounts assigned to applications or services that operate in the background of your IT environment.
Access Accumulates Over Time
User accounts require access rights and permissions at their creation, which are typically based off of group memberships. This remains true whether manual efforts or automating solutions carry out the creation and provisioning process. Some user accounts maintain the same access throughout their entire lifecycle, though most will see changes. Without regular reviews, nearly every user account risks accruing excess privileges.
Scenarios that contribute to (or require) access changes for a user account include:
Ad Hoc Projects or Assignments
When an employee receives an ad hoc project or assignment, they may require additional access rights. The project’s relevant files and data may be stored in a specific share or folder. Certain applications or licenses (e.g., Adobe) might be required for the project.
Promotions, Role Changes, or Re-Orgs.
These more permanent status changes almost always result in the need for new access. Even employees only moving geographically probably require revised access to physical buildings and infrastructure. If users moving hierarchically (or laterally) continue working with the same resources as before, they may require elevated permissions. For example, a standard user’s “read” access may need updating to a manager’s “read/write” access.
Access Removal – The Second & Most Forgotten Step
Access remains a two part process: provisioning and removal. When an employee moves within an organization and has their access rights updated, those no longer necessary must be removed. Access granted for a project must be reviewed and removed after its completion if no longer necessary for the user. Too often, however, the second part goes unaddressed.
Many organizations skip these review and reconciliation steps due to the laborious, time-intensive effort required for manual audits and adjustments. Further, granting excessive permissions simply due to short term ease remains a common but extremely risky practice with manual provisioning. For example, someone may over-provision administrator rights to a normal user to prevent under-provisioning.
Giving away the “keys to the kingdom” is never a smart solution. Without review, your organization may have untold numbers of users navigating your environment with advanced privileges. Service accounts make this practice of just over-assigning elevated privileges particularly problematic. Combining too much access with service accounts’ background nature makes for a dangerous situation in the event of a breach. Unfortunately, there is no “set and forget” method to make things easy when it comes to identity management.
Consequences of Unchecked Privilege Creep
Regulatory compliance, security vulnerabilities, network pollution, and unnecessary license costs serve as the primary reasons for review and reconciliatory efforts.
Regulatory Compliance/Segregation of Duties (SoD)
When access accumulates, employees run a greater risk of compliance violations linked to Segregation of Duty (SoD) efforts. SoD enforces the operational checks and balances that prevent noncompliance, fraud, and error by breaking up a process amongst employees or business units. Most often, this leads to the distribution of process execution and its verification—often involving multiple authorization steps.
The longer an employee remains with an organization, the more likely promotions or increased role responsibilities become. If their role expands over time from working on a process to its verification, they may be unknowingly violating SoD. With accumulated account privileges, many SoD violations become inadvertent, though just as risky for the organization.
Security Risk
Unchecked access accumulation exacerbates many security breaches. A breach compromises everything a user holds authorized access to. An intruder’s reach may be greater than anticipated or untraceable for some time if old access rights lack updates.
Network Pollution & Unnecessary License Costs
When users accumulate access, they gradually transform your IT environment into a tangled up spider web. If you’ve ever spent time untangling cords or a string of lights, you know how difficult the untangling becomes. If your organization is subject to third-party audits and compliance reviews, the effort to manually untangle your environment requires sitting down with stakeholders and managers to painstakingly revise your entire environment.
Implementing Least Privilege
Implementing least privilege requires auditing your environment to update access rights and the restricted use of privileged accounts. Internal audits are crucial for proper access control. Automated solutions enforce configured access rights and provide business intelligence reporting to drastically reduce the effort of manual reviews. Using these reports, managers and IT can collectively keep access safe and compliant.
Limiting access should also be enforced with everyday activity. Whenever administrators need to utilize their elevated permissions, they should log in to privileged accounts to do so. After the task is complete, they should log out. At all other times, ever user should use their most restricted accounts—from C-level executives to entry-level employees. Privileged access management reduces the risk of human negligence, particularly regarding sensitive data.
