OAuth is, simply put, a protocol and login method that confirms user identities based on existing, verified authentication. When you log in to an app or online site and select the “Login with Facebook” or similar option, that authentication method uses OAuth.
Apps and sites leverage OAuth to provide secure access to their portals so that users can seamlessly interact with third-party apps and sites without entering credentials for every new login. In other words, OAuth makes it possible for a user to access a site via their identity from another one. Additional capability, such as social media sharing, is enabled by OAuth as well. For example, a user authorizes access to one site (let’s use ESPN.com) to post updates to the user’s Facebook timeline without ESPN possessing the Facebook password.i
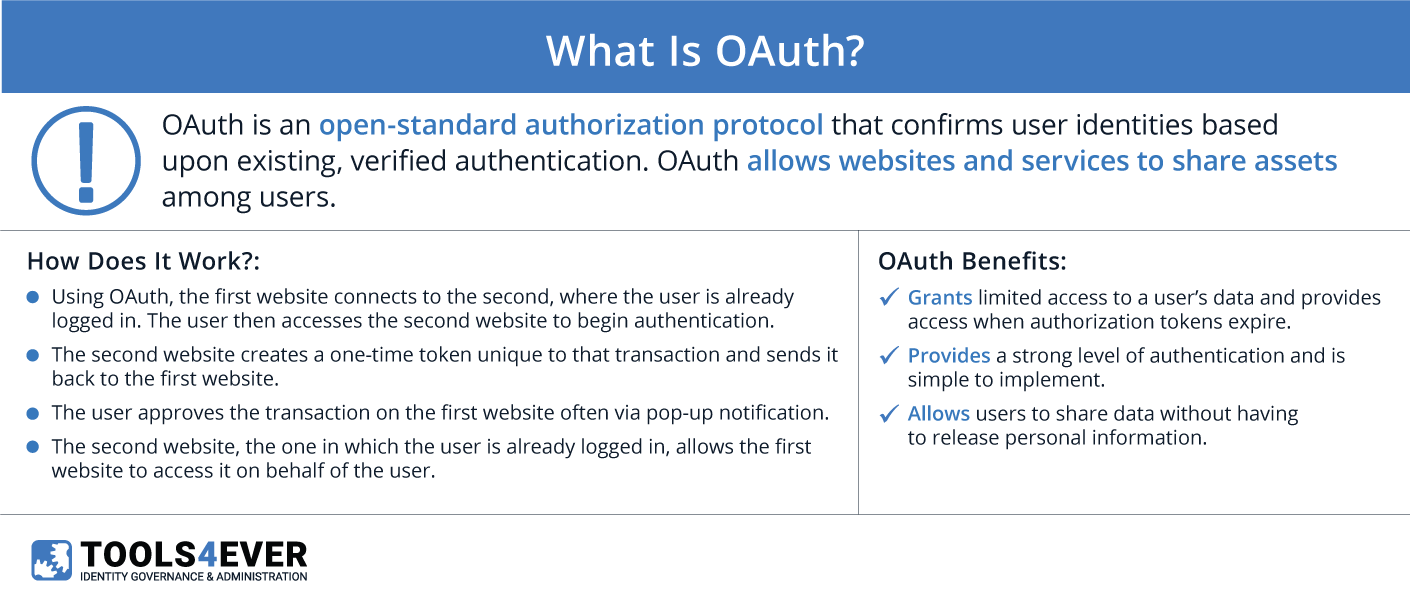
A more technical definition for OAuth would be: a secure, third-party, user-agent delegated method defined as an open-standard authorization protocol that describes how separate servers and services can safely allow authenticated access to their assets without sharing the initial login credentials.
Using OAuth
Through OAuth, the user clicks on an access rights icon that’s linked to the other website (e.g., Facebook, Google). The website the user has already logged into verifies their identity and the new site or app uses that authentication to permit access. The two sites do not share password data. Instead, they use authorization tokens to verify the user’s identity and all parties involved (user and the two sites) work in concert to complete a transaction.
OAuth is not just used for identity sharing between websites, but also facilitates the sending of cloud-stored files between users on different systems.i
OAuth 2.0
Today, we use OAuth 2.0—a complete redesign and not compatible with the initial iteration. Insiders and experts generally agree that OAuth 2.0 is faster and less complicated than its predecessor, despite containing more steps in its processes.i Released in 2012, OAuth 2.0 adopters include industry stalwarts such as Google, Facebook, Amazon, Instagram, LinkedIn, Netflix, and many more.
If a user has already signed into one service and then wants to start a transaction that needs to access a different service, the following OAuth 2.0 steps will occur (simplified in the following example):
- Using OAuth, the first website (e.g. ESPN) connects to the site where the user is already logged in (e.g., Google, Facebook) to begin authentication.
- The second site creates a one-time token and secret, unique to the transaction, which is sent back to the first site.
- The user approves the transaction on the first website.
- The second website lets the first website access its site on behalf of the user.
OAuth’s Central Components
OAuth is built on the following central components:
- Scopes and Consent
- Actors (i.e., Resource Owner, Resource Server, Client, and Authorization Server)
- Tokens
- Flows
The scope is a security feature in OAuth 2.0 that can limit an application’s access to only what is necessary for a user’s account. Consent refers to the user-granted permission to allow access.
There are four actors in OAuth: the resource owner, the resource server, the client, and the authorization server. The resource owner is a user who accesses the information/resource on the resource server. The resource server is the service that provides access to data. The client is the application that wishes to access the user’s data. The authorization server is the main engine of OAuth and where the client application is registered.
Access tokens are used to make API requests on behalf of a user. A client is required to complete this task to receive an access token from the authorization server.
OAuth Security
For all of OAuth’s many benefits, it requires an outside protection protocol to provide security. OAuth 2.0 does not define or support encryption, signature, or client verification.ii This means that all parties involved in the transaction must require outside protection protocol, such as Transport Layer Security (TLS). TLS is a cryptographic protocol that offers communications security over a computer network.iii
Since its introduction, OAuth quickly became the industry standard. With almost a decade’s worth of use, OAuth 2.0 remains in extensive usage on some of the world’s most influential websites.
i. What is OAuth? Definition and How it Works
ii. What is OAuth? How the open authorization framework works
iii. Transport Layer Security (TLS)
